Charming Kitten Returns with WhatsApp, LinkedIn Effort
The Iran-linked APT is targeting Israeli scholars and U.S. government employees in a credential-stealing effort.
The Iran-affiliated APT known as Charming Kitten is back with a new approach, impersonating Persian-speaking journalists via WhatsApp and LinkedIn, in order to con victims into opening malicious links. The targets are Israeli scholars from Haifa and Tel Aviv universities, and U.S. government employees, researchers said.
According to an analysis from Clearsky, the latest gambit was first spotted in July. The attackers have been pretending to be known writers for the Deutsche Welle and/or Jewish Journal outlets, and approach targets via email, and WhatsApp messages and calls. To lend verisimilitude to their impersonations, the cybercriminals also set up fake LinkedIn profiles corresponding to the journalists’ names, and have been sending out LinkedIn messages to corner victims as well. The end game is to convince a target to click on a malicious link, which takes users to a phishing page to steal credentials.
“The malicious link is embedded in a legitimate, compromised Deutsche Welle domain, with waterhole methods,” according to a writeup from Clearsky, issued last week. “Each victim receives a personalized link, tailored to their specific email account. We identified an attempt to send a malicious ZIP file to the victim as well, additional to a message that was sent to the victim via a fake LinkedIn profile.”
This approach is a marked departure from Charming Kitten’s usual M.O., which tends to rely on emails and SMS.
“These two platforms enable the attacker to reach the victim easily, spending minimum time in creating the fictitious social-media profile,” according to Clearsky. “However, in this campaign Charming Kitten has used a reliable, well-developed LinkedIn account to support their email spear-phishing attacks…[we also] observed a willingness of the attackers to speak on the phone directly with the victim, using WhatsApp calls, and a legitimate German phone number. This [tactic, technique and procedure] (TTP) is uncommon and jeopardizes the fake identity of the attackers.”
A fake LinkedIn page.
To get around the potential language issue, Charming Kitten generally chooses to impersonate Persian- or Farsi-speaking journalists, to neutralize detection through accent while having the phone call. Clearsky researchers pointed out that a cadre of Deutsche Welle reporters, for instance, are actually originally from Iran.
Highly Targeted
The most recent campaign had a few different prongs, but email was the initial attack vector across the board.
According to the analysis, some emails impersonated an Iranian Deutsche Welle journalist that speaks fluent Farsi with a local accent. Others impersonated an Israeli scholar from Tel Aviv University, with emails inviting targets to an alleged Zoom meeting in Hebrew. Yet others impersonated a reporter from Jewish Journal asking the target to join a webinar on “citizenship and freedom of girls and women in Iran and it’s future.”
In all cases, the attackers attempt to get a conversation going in order to establish trust. For instance, in the case of the Jewish Journal webinar, the attackers tried to entice the victim with nominating them as its main speaker, “chosen from more than a hundred participants.”
After these conversations with the target, the attacker requests that they switch to WhatsApp for further conversation, according to the analysis – attempting to engage the target via multiple messages for up to 10 days.
“Charming Kitten sent multiple and repeating messages, sometimes in very short time, until the target responded,” researchers wrote. “The messages were sent from a German number (prefix +49) to create a sense of credibility, and the WhatsApp account bears the image of the journalist being impersonated.” If the victim is not willing to share a personal phone number, the attackers will send the person a message from the fake LinkedIn accounts.
These second-stage messages contain malicious links that purport to lead to registration for various online calls or events. The link will take users to a page where they can “activate their accounts” by signing up on the site “Akademie DW” (which is actually just a phishing page). The malicious link pointing to this page was most recently hosted on a Deutsche Welle legitimate domain (dw[.]de), the researchers said.
“Each victim receives a personalized link for their own email address – the word ‘?id=’ followed by the word ‘SSH’ and three sets of five letters and numbers, “according to the researchers. On the phishing page, “If the victim enters their correct password, they are sent to a two-factor authentication (2FA) page,” said the researchers. “A wrong password produces an error message. The attackers will then pressure the victim to try again using their university email.”
The attackers also offer to engage in a direct phone call with the targets to help them with the process.
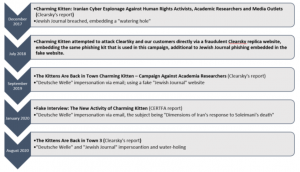
A timeline of Charming Kitten activity.
Charming Kitten, a.k.a. APT35 or Ajax, has been active since 2014. It’s known for politically motivated and socially engineered attacks, and often uses phishing as an attack vector. Its primary targets are Iranian academia experts, human-rights activists, journalists, the Baha’I community, ambassadors and former employees of the U.S. State Department, and COVID-19-related organizations such as Gilead and the World Health Organization.
The group was also recently seen trying to hack into email accounts tied to the Trump 2020 re-election campaign, ramping up those efforts with new spearphishing tactics. This is also only the latest campaign where the group has impersonated journalists. In February, the group purported to be from the Wall Street Journal, and was seen emailing a victim to ask for an interview in an effort to gain trust.

Comments
Post a Comment